Splunk Output
The Splunk Output transformation step enables you to connect to a Splunk server and write events to a Splunk index. By default, the step writes events as name value pairs separated by newline characters, but can also write arbitrary formats by customizing event data.
Prerequisites
Before using the Splunk Output step, you must have read and write access to a Splunk server. Please contact the Splunk system administrator for host and port details. To learn more about Splunk, see their online documentation.
General
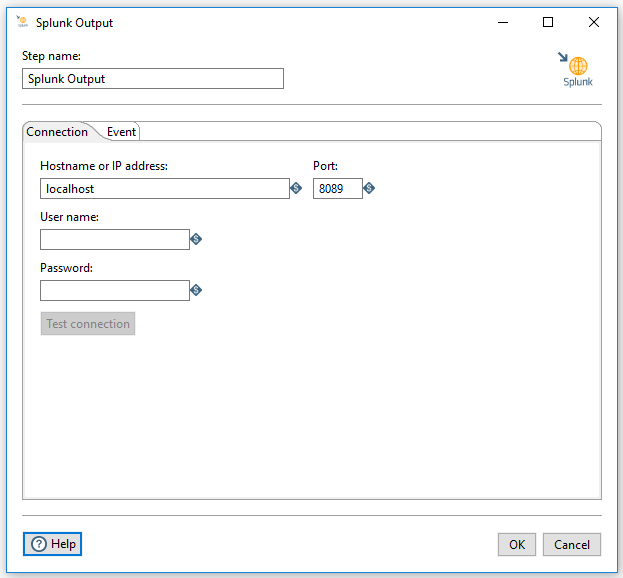
Enter the following information in the transformation Step name field.
- Specifies the unique name of the Splunk Output step on the canvas. The Step Name is set to Splunk Output by default.
Options
The Splunk Output step features two tabs with fields and options for defining Splunk a connection and event results. Each tab is described below.
Connection tab
In this tab, you can define the following properties, as described in the table below.
| Option | Description |
| Hostname or IP address | Specifies the network name or address of the Splunk instance or instances. |
| Port | Indicates the port number of the Splunk (splunkd) server. The default value is 8089, but your administrator may have changed the port number. |
| User name | Specifies the user name required to access the Splunk server. |
| Password | Indicates the password associated with the User name. |
| Test connection | After you define the connection, you can test it by clicking this button. |
Event tab
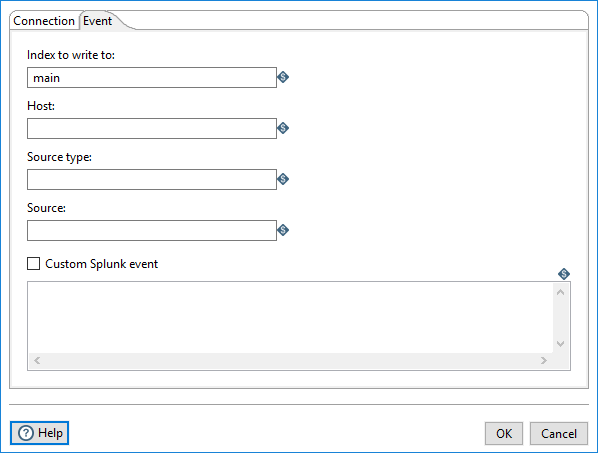
In this tab, you can define the following event properties and options, as described in the table below.
| Option | Description |
| Index to write to | Specifies the Splunk index where the events are stored. Usually, this is the main index. Check your Splunk server for a list of available indices. This field can be a parameter with incoming fields (?{<Field>}) or transformation parameters (${Parameter}). |
| Host | Indicates the hostname of the original event host. If you want to gather data from a router and write it to Splunk, use the router's host name. This field can be a parameter with incoming fields (?{<Field>}) or transformation parameters (${Parameter}). |
| Source type | Indicates the format type of the event data. The list of known source types appears here. To define a new format, follow these instructions. |
| Source | Indicates the source of the event data. See Splunk documentation for more details. |
| Custom Splunk event | If checked, enables the Splunk Event Data option and allows you to customize the data coming into Splunk. This is useful if you want to write a different format than the default, which is name value pairs separated by newline characters. |
| Splunk Event Data | Allows you to specify customized event text. This field can be a parameter with incoming fields (?{<Field>}) or transformation parameters (${Parameter}). |
Metadata injection support
All fields of this step support metadata injection. You can use this step with ETL metadata injection to pass metadata to your transformation at runtime.

